Verifying the new RDP port At this point your remote computer is all set to use a custom port for Remote Desktop. It is important to note that specific security layer for RDP connections needs to.
Can The Gorilla Deliver Assessing The Security Of Google S New Thread Internet Of Things Iot Protocol Csiac
Dive into the various segments of network security and learn how they overlap and interact with each other.
. It runs over the SSH protocol. Once the remote desktop service is restarted the target computer will start listening on a new custom RDP port number. Note for servers running Remote Desktop Services RDS.
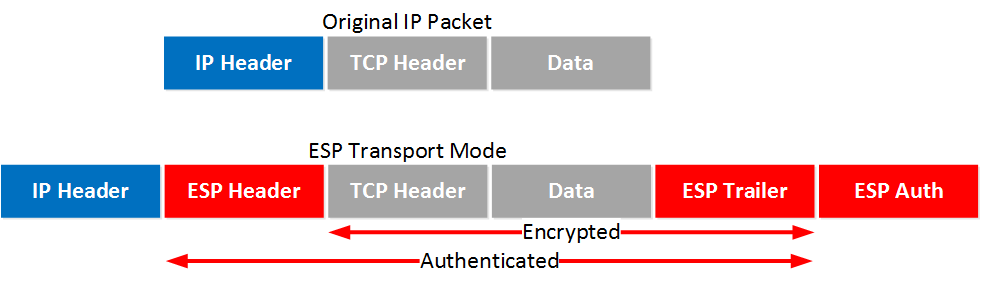
Chat The server can also set cookie-related option fields to _set_ cookies as described in. Its so widely used I would be shocked to meet a sysadmin that hasnt used it. ESP adds its own header and a trailer to each data packet.
SFTP has pretty much replaced legacy FTP as a file transfer protocol and is quickly replacing FTPS. A code received by notification or a biometric verification. SSH is a cryptographic protocol that creates a tunnel between two remote computers.
It supports the full security and authentication functionality of SSH. Last July McAfee ATR did a deep dive on Remote Desktop Protocol. 14Closing Handshake _This section is non-normative_ The closing handshake is far simpler than the opening handshake.
Network security isnt a one-size-fits-all strategy. Billions of people the world over depend on Wi-Fi in their homes and businesses to shop bank coordinate life and stay connected. This update does not include Remote Desktop Protocol 81 server-side components for Windows 7 virtual desktops.
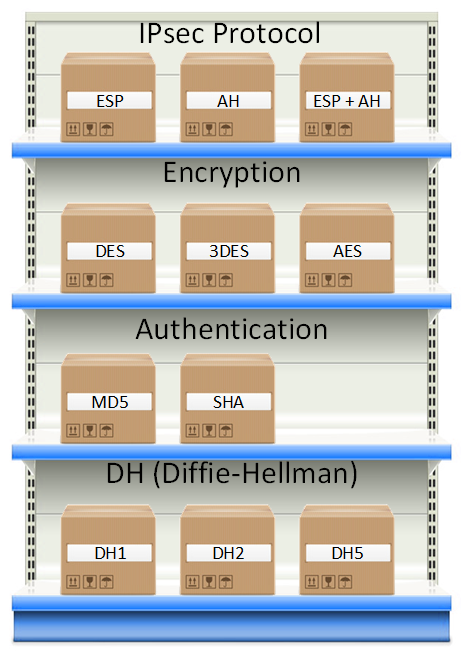
If you run the following PowerShell command on a remote computer it will give you the new endpoints. Still using a connection pool improves performance if you open and close connections a lot. IPsec is a suite of protocols that are used to secure internet communicationsin fact the name itself is an abbreviation for Internet Protocol Security.
The default security layer in RDP is set to Negotiate which supports both SSL TLS 10 and the RDP Security Layer. However if you. Wi-Fi is an integral part of daily life.
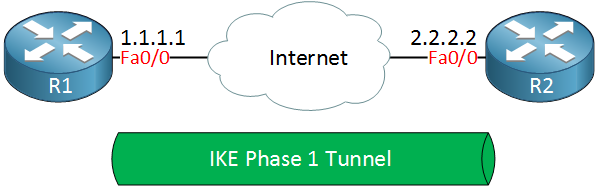
SA refers to a number of protocols used for negotiating encryption keys and algorithms. Remote Desktop Protocol RDP is a tried and tested protocol that sysadmins have been using for years. Once the tunnel is established the remote system shell is visible and shell commands can be securely transmitted across the connection.
In 2020 enterprises shifted to. This type of security system uses two different keys to encrypt communications between two parties. In other words this.
Therefore the entire suite is commonly referred to as TCPIPTCP provides reliable ordered and error-checked delivery of a stream of octets bytes between applications running. Multi-factor authentication adds an additional layer of protection by requiring the user to provide a security token eg. In this article well cover everything about remote desktop security and its risks.
As an easy-to-use remote access tool it supports basic file sharing wake-on-LAN remote printing black screen for private sessions mobile-to. It is based on the Mini Connection Pool Manager from Christian dHeureuse. What is IPsec.
The SSH protocol was created to replace insecure protocols for remote connections. This protocol secures communications by using whats known as an asymmetric public key infrastructure. Using a Connection Pool.
The protocol is called Transport Layer Security TLS although formerly it was known as Secure Sockets Layer SSL. Here is an illustration of an SSH handshake. Co-existence with the RDP 80 update.
5 trends in enterprise networking that defined 2021. But just because something is widely used doesnt mean that its without its flaws. Securing Wi-Fi connections is an important element of securing personal data and Wi-Fi Alliance has been on the forefront of evolving Wi-Fi security as the number of Wi-Fi devices in use worldwide has.
One of the most common SA protocols is Internet Key Exchange IKE. IPsec was first codified. The Transmission Control Protocol TCP is one of the main protocols of the Internet protocol suiteIt originated in the initial network implementation in which it complemented the Internet Protocol IP.
For H2 opening a connection is fast if the database is already open. And this became a prime opportunity for attackers to launch RDP Remote Desktop Protocol attacks on public-facing servers with unpatched vulnerabilities. It provides all the functionality offered by these protocols but more.
Remote Desktop has been host to a wide array of vulnerabilities over the. Finally while the Internet Protocol IP is not part of the IPsec suite IPsec runs directly on top of IP. SFTP SSH File Transfer Protocol is a secure file transfer protocol.
A simple connection pool is included in H2. New features for remote connections to Windows 81 or Windows Server 2012 R2. 2574819 An update is available that adds support for DTLS in Windows 7 SP1 and Windows.
RFC 6455 The WebSocket Protocol December 2011 Sec-WebSocket-Protocol. Its never too late to work towards ensuring remote desktop security. Either peer can send a control frame with data containing a specified.

Taskbar Not Visible In Remote Desktop On Windows 10 Remote Desktop Protocol Settings App Background Process
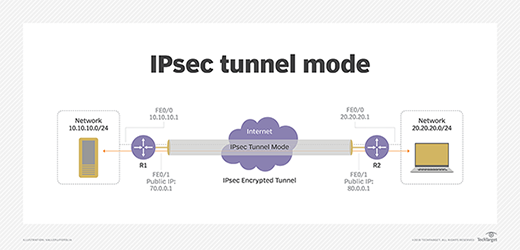
Ipsec Internet Protocol Security
Ipsec Internet Protocol Security

What Is Internet Protocol Security Vpn Ipsec Vpn Definition From Techopedia
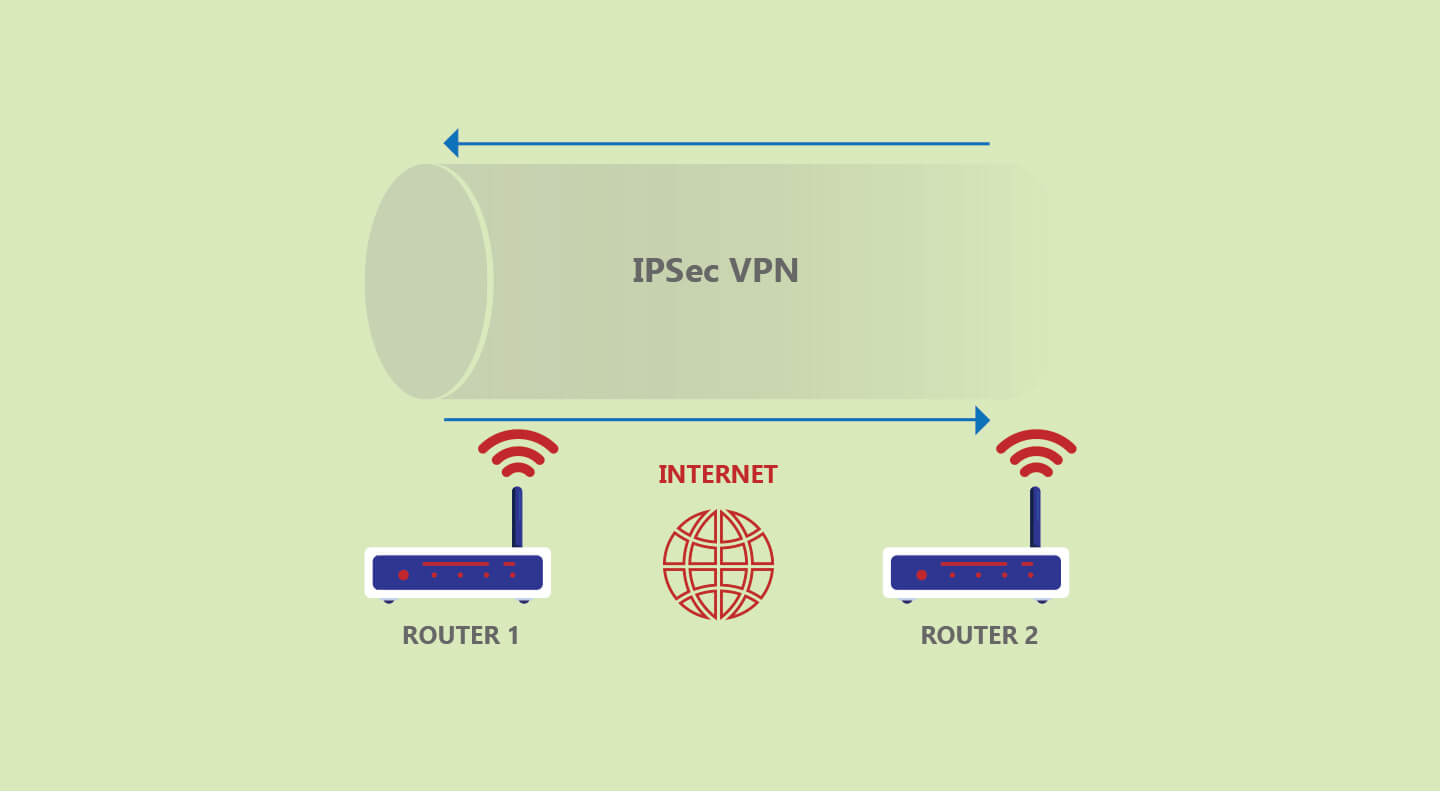
Ipsec Vpn What It Is And How It Works

0 comments
Post a Comment